Yet another fake ransom requestYet another example of mass-mailing camouflaged as a not-so-clever ransom request. Also in this case, the spammer hopes to convince a few easily fooled people to part with their hard-earned cash. As always in these cases, the spammer has no "compromising" information about you, is not going to do anything against you after the deadline expires, and the whole thing is just a simple extortion attempt. If you don't pay, absolutely nothing will happen to you. In this case, it is a little unusual that the text was sent in plain. Many spammers are a little more knowledgable and send their e-mails as attached images, in order to circumvent the spam filters of mail servers. In fact, the X-Spam-Score header (below) shows that this e-mail was automatically identified as a very likely spam. The text of the e-mail, including the headers because they contain information of potential technical interest (some of it redacted to hide my own information): Return-path: <bethanykingsmill5463@spambog.com> One thing we can note is that spambog.com is most likely hosted and/or registered by anexia-it.net, an Internet provider located in Austria, Germany and the United States. The mail server/relay at spambog.com is strongly suspected to be used for various types of fraud. Also, the 197.2.190.119 IP address used to send this e-mail through the illegal e-mail relay at spambog.com belongs to Algerian IT provider Topnet, which does not publish an abuse-report address (apparently they prefer to let the scammers among their customers free to do whatever they want). A report on the spambog.com domain generated by www.ipqualityscore.com is shown below. It is interesting to learn that this domain has been in use for 17 years, during which the ISP hosting this e-mail server has probably received thousands of complaints. This also shows the priorities of this ISP when faced with the choice between a good reputation vs. customers' money. Most large e-mail services like Gmail have long since banned this domain and its ISP. I reported the above e-mail to Anexia, but I don't expect a reply (I will update this page if I do, but I am not holding my breath), let alone any action by Anexia against this mail server apparently designed to support criminal activities. I configured my firewall to drop any future network traffic from the IPv4 address block 37.120.160.0 - 37.120.163.255 into a tame black hole, and my e-mail client to delete any incoming mail containing "spambog" in any header, and I expect this is the last I will hear from them until they will start using a different ISP. 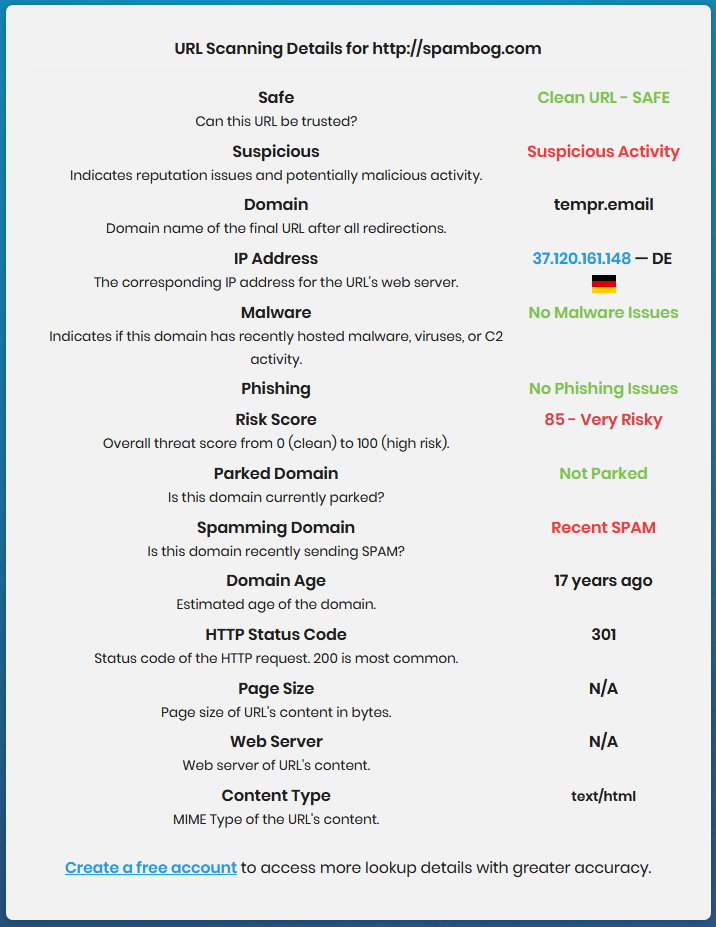
Aside from the fact that watching pornography on the Internet is not a crime in any country, and that many millions of people do it every day, you need not be afraid of anything this would-be scammer could do to you, for the simple reason that he knows nothing at all and can do nothing at all. He has not planted spyware on your computer, he has no clue what you do or don't do on the Internet, and he has no access to your contact lists, or e-mail accounts, or social media accounts. The only thing he has is a list of e-mail addresses, to which he is sending this type of mass-mailing in the hope that two or three people will believe his threats and send him their money. One thing we can do, on the other hand, is keep an eye on the scammer's Bitcoin account, now that he has generously provided this information to us. At this link you can see all incoming and outgoing payments done with this account. At the time of writing, the account has already received the requested ransom from one fool, who has (unnecessarily) voluntarily given away 1,252.76 USD from his savings by using his newly created Bitcoin wallet n. bc1q932hj7zyy374pmdy0avcvxpzcv4ekgrd2jhu8c. You can track the transaction, for example, at this link, and in this way see any other transactions recently carried out with the same wallet, the account number at the other end of each transaction, and so on, and so forth. Although Bitcoin wallets are anonymous, in a general sense and to the general public, authorities can indeed seize the contents of a wallet by issuing the required warrants to the company holding the top-level keys of the blockchain. Therefore, the contents of a wallet are in no way out of the reach of authorities, and any attempt to convert Bitcoin into cash through bank services is of course far from anonymous. By checking this link now and then, you can see how many fools have fallen for this scam. You can then trace back the transaction to the original Bitcoin wallet and see all other transactions carried out from the same account. Let's look above the shoulder of anyone who pays a ransom, because this is the only thing one should really be ashamed of. Don't become yet another fool. Never pay a ransom.
|